Introduction:
----------------
Tcp/IP is the common protocol used between computers and network devices for communication.
And if you will talk about the internet , This is the correct example of this model. Internet work
based on TCP/IP.
Application Layer:-
This layer of the TCP/IP model consists various protocol This includes interaction with the application, data translation and encoding, dialogue control and communication coordination between systems
The following are few of the most common Application Layer protocols used today:
TELNET:-
Telnet is a terminal emulation protocol used to access the resources of a remote host.
It is a text-based connection and usually provides access to the command line interface of the host. Remember that the application used by the client is usually named telnet also in most operating systems. You should not confuse the telnet application with the Telnet protocol.
HTTP:-
The Hypertext Transfer Protocol is foundation of the World Wide Web. It is used to transfer Webpages and such resources from the Web Server or HTTP server to the Web Client or the HTTP client. When you use a web browser such as Internet Explorer or Firefox, you are using a web client. It uses HTTP to transfer web pages that you request from the remote servers
FTP –
File Transfer Protocol is a protocol used for transferring files between two hosts. Just like telnet and HTTP, one host runs the FTP server application (or daemon) and is called the FTP server while the FTP client runs the FTP client application. A client connecting to the FTP server may be required to authenticate before being given access to the file structure. Once authenticated, the client can view directory listings, get and send files, and perform some other file related functions. Just like telnet, the FTP client application available in most operating systems is called ftp. So the protocol and the application should not be confused.
SMTP –
Simple Mail Transfer Protocol is used to send e-mails. When you configure an email client to send e-mails you are using SMTP. The mail client acts as a SMTP client here. SMTP is also used between two mails servers to send and receive emails. However the end client does not receive emails using SMTP. The end clients use the POP3 protocol to do that.
TFTP –
Trivial File Transfer Protocol is a stripped down version of FTP. Where FTP allows a user to see a directory listing and perform some directory related functions, TFTP only allows sending and receiving of files. It is a small and fast protocol, but it does not support authentication. Because of this inherent security risk, it is not widely used.
DNS –
Every host in a network has a logical address called the IP address (discussed later in the chapter). These addresses are a bunch of numbers. When you go to a website such as www.cisco.com you are actually going to a host which has an IP address, but you do not have to remember the IP Address of every WebSite you visit. This is because Domain Name Service (DNS) helps map a name such as www.cisco.com to the IP address of the host where the site resides. This obviously makes it easier to find resources on a network. When you type in the address of a website in your browser, the system first sends out a DNS query to its DNS server to resolve the name to an IP address. Once the name is resolved, a HTTP session is established with the IP Address.
DHCP –
As you know, every host requires a logical address such as an IP address to communicate in a network. The host gets this logical address either by manual configuration or by a protocol such as Dynamic Host Configuration Protocol (DHCP). Using DHCP, a host can be provided with an IP address automatically. To understand the importance of DHCP, imagine having to manage 5000 hosts in a network and assigning them IP address manually! Apart from the IP address, a host needs other information such as the address of the DNS server it needs to contact to resolve names, gateways, subnet masks, etc. DHCP can be used to provide all these information along with the IP address.
Transport Layer-
segments great chunks of data received from the upper layer protocols. Establishes and terminates connections between two computers. Used for flow control and data recovery
Two protocols available in this layer are Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). TCP is a connection oriented and reliable protocol that uses windowing to control the flow and provides ordered delivery of the data in segments. On the other hand, UDP simply transfers the data without the bells and whistles. Though these two protocols are different in many ways, they perform the same function of transferring data and they use a concept called port numbers to do this. The following sections cover port numbers before looking into TCP and UDP in detail.
Port Numbers
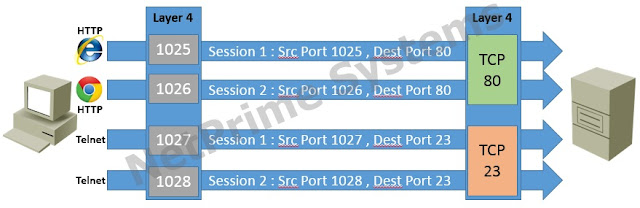
A host in a network may send traffic to or receive from multiple hosts at the same time. The system would have no way to know which data belongs to which application. TCP and UDP solve this problem by using port numbers in their header. Common application layer protocols have been assigned port numbers in the range of 1 to 1024. These ports are known as well-known ports. Applications implementing these protocols listen on these port numbers. TCP and UDP on the receiving host know which application to send the data to based on the port numbers received in the headers.
On the source host each TCP or UDP session is assigned a random port number above the range of 1024. So that returning traffic from the destination can be identified as belonging to the originating application. Combination of the IP address, Protocol (TCP or UDP) and the Port number forms a socket at both the receiving and sending hosts. Since each socket is unique, an application can send and receive data to and from multiple hosts. Figure 1-10 shows two hosts communicating using TCP. Notice that the hosts on the left and right are sending traffic to the host in the center and both of them are sending traffic destined to Port 80, but from different source ports. The host in the center is able to handle both the connections simultaneously because the combination of IP address, Port numbers and Protocols makes each connection different.


Reliable Delivery with Error recovery – When the destination receives the last segment in the agreed window, it has to send an acknowledgement to the source. It sets the ACK flag in the header and the acknowledgement number is set as the sequence number of the next byte expected. If the destination does not receive a segment, it does not send an acknowledgement back. This tells the source that some segments have been lost and it will retransmit the segments. Figure 1-13 shows how windowing and acknowledgement is used by TCP. Notice that when source does not receive acknowledgement for the segment with sequence number 2000, it retransmits the data. Once it receives the acknowledgement, it sends the next sequence according to the window size.
Ordered Delivery – TCP transmits data in the order it is received from the application layer and uses sequence number to mark the order. The data may be received at the destination in the wrong order due to network conditions. Thus TCP at the destination orders the data according to the sequence number before sending it to the application layer at its end. This order delivery is part of the benefit of TCP and one of the purposes of the Sequence Number.
Connection Termination – After all data has been transferred, the source initiates a four-way handshake to close the session. To close the session, the FIN and ACK flags are used.


User Datagram Protocol (UDP)
The only thing common between TCP and UDP is that they use port numbers to transport traffic. Unlike TCP, UDP neither establishes a connection nor does it provide reliable delivery. UDP is connectionless and unreliable protocol that delivers data without overheads associated with TCP. The UDP header contains only four parameters (Source port, Destination Port, Length and Checksum) and is 8 bytes in size.
At this stage you might think that TCP is a better protocol than UDP since it is reliable. However you have to consider that networks now are far more stable than when these protocols where conceived. TCP has a higher overhead with a larger header and acknowledgements. The source also holds data till it receives acknowledgement. This creates a delay. Some applications, especially those that deal with voice and video, require fast transport and take care of the reliability themselves at the application layer. Hence in lot of cases UDP is a better choice than TCP.
Internet Layer
Once TCP and UDP have segmented the data and have added their headers, they send the segment down to the Network layer. The destination host may reside in a different network far from the host divided by multiple routers. It is the task of the Internet Layer to ensure that the segment is moved across the networks to the destination network.
The Internet layer of the TCP/IP model corresponds to the Network layer of the OSI reference model in function. It provides logical addressing, path determination and forwarding.
The Internet Protocol (IP) is the most common protocol that provides these services. Also working at this layer are routing protocols which help routers learn about different networks they can reach and the Internet Control Message Protocol (ICMP) that is used to send error messages across at this layer.
Almost half of the book is dedicated IP and Routing protocols so they will be discussed in detail in later chapters, but the following sections discuss these protocols in brief.
Internet Protocol (IP)
The Internet layer in the TCP/IP model is dominated by IP with other protocols supporting its purpose. Each host in a network and all interfaces of a router have a logical address called the IP address. All hosts in a network are grouped in a single IP address range similar to a street address with each host having a unique address from that range similar to a house or mailbox address. Each network has a different address range and routers that operate on layer 3 connect these different networks.
As IP receives segments from TCP or UDP, it adds a header with source IP address and destination IP address amongst other information. This PDU is called a packet. When a router receives a packet, it looks at the destination address in the header and forwards it towards the destination network. The packet may need to go through multiple routers before it reaches the destination network. Each router it has to go through is called a hop.

There are various versions of the Internet Protocol. Version 4 is the one used today and version 6 is slowly starting to replace it which is why it’s presence has increased on the CCNA Routing & Switching 200-120 exam compared to previous CCNA exam versions. Figure 1-15 shows the header structure of IPv4. The following fields make up the header:
Version – IP version number. For IPv4 this value is 4.
Header Length – This specifies the size of the header itself. The minimum size is 20 bytes. The figure does not show the rarely used options field that is of a variable length. Most IPv4 headers are 20 bytes in length.
DS Field – The differentiated Services field is used for marking packets. Different Quality-Of-Service (QoS) levels can be applied on different markings. For example, data belonging to voice and video protocols have no tolerance for delay. The DS field is used to mark packets carrying data belonging to these protocols so that they get priority treatment through the network. On the other hand, peer-to-peer traffic is considered a major problem and can be marked down to give in best effort treatment.
Total Length – This field specifies the size of the packet. This means the size of the header plus the size of the data.
Identification – When IP receives a segment from TCP or UDP; it may need to break the segment into chucks called fragments before sending it out to the network. Identification fields serves to identify the fragments that make up the original segment. Each fragment of a segment will have the same identification number.
Flags – Used for fragmentation process.
Fragment Offset – This field identifies the fragment number and is used by hosts to reassemble the fragments in the correct order.
Time to Live – The Time to Live (TTL) value is set at the originating host. Each router that the packet passes through reduces the TTL by one. If the TTL reaches 0 before reaching the destination, the packet is dropped. This is done to prevent the packet from moving around the network endlessly.
Protocol – This field identifies the protocol to which the data it is carrying belongs. For example a value of 6 implies that the data contains a TCP segment while a value of 17 signifies a UDP segment. Apart from TCP and UDP there are many protocols whose data can be carried in an IP packet.
Header Checksum – This field is used to check for errors in the header. At each router and at the destination, a cyclic redundancy check performed on the header and the result should match the value stored in this field. If the value does not match, the packet is discarded.
Source IP address – This field stores the IP address of the source of the packet.
Destination IP address – This field stores the IP address of the destination of the packet.