What happens, when a router receives the packet?
Upon receiving the
Packet, a router has to follow three step process before it routes the packets:
->
Routing
->
Forwarding (Switching)
->
Encapsulation
Let’s
discuss each one of them in detail
Routing Process: Routing process
is nothing but routers control plane. Router records a routing table listing
what route should be used to forward a data packet, and through which physical
interface connection. Router learns your network routes information either by
static configuration or by using dynamically configure routing protocol like
IGP (OSPF, EIGRP, RIP, IS-IS) or though Exterior routing protocol like BGP.
When router receives
any packet it has to remove Layer 2 header information present on
packet(Example:In Ethernet, source and destination Mac address present on L2
header). Once router remove L2 information it looks for Layer 3 information
available on packet that is source and destination IP address.
For moving L3 packet
between interfaces, router checks destination address and finds longest-prefix
match in IP routing table to find outgoing interface. In IPv4 router uses
longest mask to identify best routing entry for forwarding packet.
Example: Let’s assume
we have configured 3 different static routes with different subnet mask.
Sh ip route 1.1.1.1
ip route 1.1.1.0
255.255.255.0 fa0/2
ip route 1.1.0.0
255.255.0.0 fa0/1
ip route 1.0.0.0
255.0.0.0 fa0/0
In above example when
router does route lookup for destination address 1.1.1.1 out of 3 entries
router will choose longest-prefix length match entry i.e. 1.1.1.0/24 , because
destination address has most common bits matches with selected route and will
forward packet out fa0/2.
|
Destination
prefix
|
Binary
Splitting
|
|
1.1.1.1
|
00000001
00000001 00000001 00000001
|
|
1St Entry
1.1.1.0/24
|
00000001
00000001 00000001 00000000
|
|
2nd Entry
1.1.0.0/16
|
00000001
00000001 00000000 00000000
|
|
3rd Entry
1.0.0.0/8
|
00000001 00000000
00000000 00000000
|
|
|
Now for any other
destination prefix like 1.1.2.0 longest match is 1.1.0.0/16 and for 1.2.0.0 it
would be 1.0.0.0/8
Longest match possible
in IPv4 routing is /32 (255.255.255.255) and shortest match possible is default
route i.e. 0.0.0.0
->If there are multiple
routes with same subnet mask learned via same protocol by router then router
chooses lowest metric between them.
For Example: Eigrp use
composite “metric” and Ospf uses “Cost” for comparison.
->If there is multiple
routes with same subnet mask learn via different protocol on router then router
chooses lowest administrative distance (AD).
->Last and important
point is recursive lookup: which states that whenever there is route lookup
more than once it will be termed as recursive lookup. It has to be done by
router till destination address point towards any physical or logical interface.
Example:
We have a network
1.1.1.1 connected somewhere and we are reaching it by interface fa0/0 having
next-hop IP address 2.2.2.2.So we can configure static route in two different
ways either we can define next-hop IP address i.e.2.2.2.2 or we can mention
interface number fa0/0 as gateway shown below.
ip route 1.1.1.1
255.255.255.255 2.2.2.2
ip route 1.1.1.1
255.255.255.255 FastEthernet0/0
Both statements look
same although both have different meaning.When you point destination address to
next hop as exit interface you don’t need further route lookup as router assume
destination address is directly connected to that interface. But when you point
destination address to any next hop ip address, we need another route lookup
also for next hop ip address is referring as recursive lookup.
To get more
information on how static route work when you set gateway as Next-Hop IP
address or to Next-Hop interface please refer this document.
Forwarding process: It is also known as
switching process. Once router finds outgoing interface, packet move between
interfaces by switching process. This is done by process switching, fast
switching or cef switching. Forwarding can be done by using adjacency tables
reside on the route processor or on interface cards that support switching.
-> Process switching
requires the device CPU to be involved for every forwarding decision.
-> Fast switching still
uses the CPU for initially packets and to fill cache table in router. Once
initial packet has been forwarded, the information about how to reach the
destination is stored in a fast-switching cache’s .when another packet going to
the same destination, the next hop information can be re-used from the cache
and so the router processor doesn’t have to look into it, but if the
information is not cached the CPU will have to process entire packets.
-> When CEF mode is
enabled it build the CEF FIB and adjacency tables reside on the route
processor, and the route processor performs the express forwarding.
In switching process
device do actual packet link load balancing depending on the methodology we
use.
Encapsulation process: L3 header will
remain intact unchanged except for nating, vpn etc. layer 2 headers keep
changing on hop by hop basis, depending on transmission media. For transmitting
L3 packet on wire router need to find out l2 information for packets and it’s
depending on the type of media we are using for transmission.
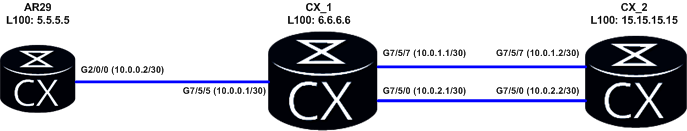
To explain
encapsulation process in bit detail, I have created a small topology shown as
below in diagram.
As discussed above,
depending on the transmission media (In this example transmission media is
Ethernet) MAC address in layer 2 headers will keep changing on hop by hop
basis.
To generate some
traffic, Lets ping from R3 to R2 interface address.As soon as R1 receives the
packet from R3, It will remove the L2 information sent by R3 and check the L3 information
that is source (20.1.1.2) and destination address (10.1.1.1) available on
packet. Then it will look into its routing table to find out going interface
i.e. fa0/0 in above example. Once router identify outgoing interface it will
attach L2 header before putting the packet on the wire. So now R1 will attach
its own interface Mac address as source and R2’s as destination mac address.
Address resolution
protocol (ARP) table on R1:
To get closer packet
level overview, I have also attached some packet capture taken on R1's
interfaces.
Packet capture on R1’s
Fa0/1:
Packet capture on R1’s
Fa0/0:
Multipoint Broadcast
Interfaces, Routing, and ARP
When the router needs to route a
packet which matches an entry in the routing table with a next-hop value, it
performs Layer 3 to Layer 2 resolution for the next-hop address. If it matches
an entry in the routing table with just the outgoing/exit local interface,
without a next-hop value, it performs Layer 3 to Layer 2 resolution for the
final destination of the IP packet.
From a design perspective, the ideal
solution for this problem is to never configure a static route to point out a
multipoint interface. Static routes should either point to the next-hop value
of the neighbor on the multipoint interface or point to an interface only if it
is point-to-point, such as a GRE tunnel, PPP or HDLC link.
When
you configure a static route to use an interface attached to a broadcast media
(e.g. ethernet), a Cisco router expects that the network is directly attached. As a result
it has to ARP for anything that falls within the scope of your static route.
Consider the following topology:
Chesterton# ip route
1.2.3.4 255.255.255.255 eth0/0
In this configuration,
router Chesterton has to make an ARP
request for 1.2.3.4/32 and broadcast it via Ethernet0/0. He is now totally
reliant on one of two possiblities:
1. A Static ARP entry
2. Vegas will “proxy-arp” his request
If neither of these
conditions exists, he won’t be able to reach his destination. The topology
presented is a minor case, and as a result there’s no real problem with it. If
we were to increase the load, we begin to see a greater set of problems.
Chesterton# no ip route
1.2.3.4 255.255.255.255 eth0/0
Chesterton# ip route
0.0.0.0 0.0.0.0 eth0/0
Now that we’ve added a
little more scope for router “Chesterton”
to look for, we have a higher possibility for impact. If he attempts to reach
8.8.8.8, 180.0.123.12, and 5.4.3.2 we will see arp entries for each address
(all of which will have the MAC address of router Vegas’ e0/0 interface). If
there is a lot of traffic from Chesterton to the internet, we have the
potential to fill up the arp-cache; thus, causing memory problems that will
lead to forwarding problems.
Bottom Line (TL;DR
version):
Yes, you can do it and it shouldn’t be a big deal on a small deployment;
However, it’s bad practice and could really backfire in a big network.
When configuring a static route, the
following options are available:
1-specify only the
next-hop value; route is valid as long as a route exists for the next-hop
value.
2-Specify only the local
outgoing interface; route is valid as long as the interface is in the UP/UP
state.
3-Specify both next-hop value and local outgoing interface.
When the third option is selected, the
local outgoing interface behaves like a condition for the next-hop value and
should be read like: this static route is valid only if the configured next-hop
value is reachable over the configured interface, which means as long as the
interface is in the UP/UP state and has nothing to do with IP/ARP/NHRP
functionality with the next-hop.