Introduction
The next step of this workshop lab will set up eBGP with our upstream provider so that we can see the Internet.
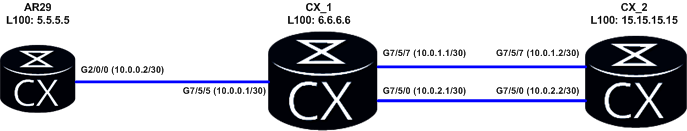
Lab Topology
The diagram below is a reminder of the lab topology:
Configuring the link to the Transit Provider
The lab instructors will be running the routers for the two Transit Providers and will have already configured them. Please remember to discuss any problems with setting up BGP with the two Transit Operators. Don’t just assume that if eBGP doesn’t come up that the lab instructors will fix the problem for you in the background.
Physical Link
Follow the guidelines in the IP Address Plan document to configure the link to the upstream. Make sure that you can ping the upstream’s router using both IPv4 and IPv6 - if it doesn’t work, investigate why not.
Here is an typical configuration sample - note that we are following the same good practices as we did when we set up the internal interfaces on our network:
interface Fastethernet 0/0
description Link to Transit Provider N
ip address <ipv4-ptp> 255.255.255.252
no ip directed-broadcast
no ip redirects
no ip proxy-arp
ipv6 address <ipv6-ptp>/127
ipv6 nd prefix default no-advertise
ipv6 nd ra suppress all
no shutdown
!
IS-IS
Do not configure IS-IS towards the upstream provider! They are not part of your autonomous system.
External BGP
We now configure eBGP with the upstream. Again, the configuration on the two transit routers will have already been completed by the instructors, so once configured, the eBGP session should just come up and work.
Don’t forget to filter what you hear from the upstream, and what you send to them. You should only accept a default route from them (they may send you more), and you should only send prefixes you originated!
Let’s set up the filters first, before we set up the eBGP session with our external neighbour. Let’s create an outbound filter for the prefixes we will send to our upstream provider. We do this for IPv4:
ip prefix-list ASX0-block permit 100.68.X.0/24
and IPv6:
ipv6 prefix-list ASX0-v6block permit 2001:DB8:X::/48
Now we need to create prefix-lists for the default route we are hearing from the upstream provider. First we create one for IPv4:
ip prefix-list DEFAULT-ROUTE permit 0.0.0.0/0
and then for IPv6:
ipv6 prefix-list DEFAULT-v6ROUTE permit ::/0
Then we can set up the eBGP configuration. Here is a configuration sample, first for IPv4:
router bgp X0
!
address-family ipv4
neighbor <ipv4-ptp> remote-as <N-ASN>
neighbor <ipv4-ptp> description eBGP with TRANSIT N
neighbor <ipv4-ptp> password BGPlab
neighbor <ipv4-ptp> prefix-list ASX0-block out
neighbor <ipv4-ptp> prefix-list DEFAULT-ROUTE in
neighbor <ipv4-ptp> activate
!
and then for IPv6:
router bgp X0
!
address-family ipv6
neighbor <ipv6-ptp> remote-as <N-ASN>
neighbor <ipv6-ptp> description eBGP with TRANSIT N
neighbor <ipv6-ptp> password BGPlab
neighbor <ipv6-ptp> prefix-list ASX0-v6block out
neighbor <ipv6-ptp> prefix-list DEFAULT-v6ROUTE in
neighbor <ipv6-ptp> activate
!
Once this has been configured, you should now see a default route coming from the upstream provider, and you should be able to see your aggregate being sent to your upstream.
If you see nothing from the upstream provider, check your filters first before asking the lab instructors. Check also with your lab instructors to make sure that they are seeing your IPv4 and IPv6 aggregates. Don’t just assume they will somehow look on your behalf.
The commands to see what you are receiving from the Transit Provider are:
show ip bgp neighbor <ipv4-ptp> routes
show bgp ipv6 unicast neighbor <ipv6-ptp> routes
and to show what you are sending to the Transit Provider:
show ip bgp neighbor <ipv4-ptp> advertised-routes
show bgp ipv6 unicast neighbor <ipv6-ptp> advertised-routes
Note that there are IPv4 versions of the IPv6 commands too, although they are a bit more to type than the versions given above:
show bgp ipv4 unicast neighbor <ipv4-ptp> routes
show bgp ipv4 unicast neighbor <ipv4-ptp> advertised-routes
Confirmation
Check on the Core, Access and Peering Routers what you now see in the BGP table. Are there differences? Can you explain what they are, and why?
Sending Default Route using IS-IS
The border router connects to the upstream provider, and therefore gives us access to the whole Internet. The upstream provider will usually send us a default route by eBGP. Once we hear this default route, how should it be propagated around the autonomous system?
It can be propagated using iBGP as we have just seen, but that tends to be non-optimal, certainly when trying to load balance between two or more transit providers, as the BGP best path is just that, the one and only best path. If we distribute the default by the IGP instead, then at least the default route becomes the nearest exit, to the nearest border router (we only have one in this lab, but a future scaled version of this network infrastructure would double up on the core, border and peering routers at least).
IS-IS by default will always originate a default route with the default-information originate command (unlike OSPF which will do it only if there is a default route in the Global RIB). So we need to fix this so that IS-IS will only announce a default if it sees the default in the Global RIB. To do this we will reuse the prefix-list we already created earlier which has the default route in it:
ip prefix-list DEFAULT-ROUTE permit 0.0.0.0/0
ipv6 prefix-list DEFAULT-v6ROUTE permit ::/0
Now we create a route-map which matches the default route, first for IPv4:
route-map DEFAULT-ORIG permit 5
match ip address prefix-list DEFAULT-ROUTE
!
and then for IPv6 (using same name, but adding v6):
route-map DEFAULT-ORIGv6 permit 5
match ipv6 address prefix-list DEFAULT-v6ROUTE
!
and finally we apply the route-map to the default-information originate command in IS-IS:
router isis asX0
default-information originate route-map DEFAULT-ORIG
!
address-family ipv6
default-information originate route-map DEFAULT-ORIGv6
!
Confirmation
Check on the Core, Access and Peering Routers what you now see in the BGP table. And look at the Routing table on each. Are there differences? Can you explain what is happening now?
RIB Failure?
What does:
show ip bgp 0.0.0.0 0.0.0.0
show ip route 0.0.0.0 0.0.0.0
and
show ipv6 route ::/0
show bgp ipv6 unicast ::/0
show you on the core router and on the peering router?
You will notice that the default route is being propagated by BGP throughout the AS.
On the core and access routers, you should see “complaints” of a RIB failure when you look at the BGP table, because IS-IS has a default route with a lower protocol distance.
On the peering router, it will complain of a RIB failure when you look at the BGP table, because there is a static default route to the Null interface.
While there is nothing wrong with a RIB failure, we can just remove the default from being propagated by the iBGP process.
Stopping default route propagation by iBGP
To do this, we go back to the eBGP session with the transit provider (on the border router), look for the default, tag it with the no-advertise community, and then the border router will no longer announce the default by iBGP.
Let’s create the route-map first - we’ll have to create one for IPv4 and another one for IPv6. We already have a prefix-list for the default route on the Border router, so we can re-use it for the route-maps we are creating, First we create the IPv4 route-map:
route-map tag-default permit 5
match ip address prefix-list DEFAULT-ROUTE
set community no-advertise
!
route-map tag-default permit 10
!
and then we create the IPv6 version:
route-map tag-v6default permit 5
match ipv6 address prefix-list DEFAULT-v6ROUTE
set community no-advertise
!
route-map tag-v6default permit 10
!
And then we apply the route-maps to the Border router. Here is a configuration sample for the Border router:
router bgp X0
address-family ipv4
neighbor <ipv4-ptp> route-map tag-default in
!
address-family ipv6
neighbor <ipv6-ptp> route-map tag-v6default in
!
Once this is done, we need to refresh the iBGP session the Border router has with the Core router:
BX# clear ip bgp X0 out
BX# clear bgp ipv6 unicast X0 out
To confirm, has the default route now disappeared from the BGP table on the Core, Access and Peering routers? If not, check your configuration, check the route-refresh command you issued above.
Testing
Once this has been completed, test the connectivity. Can you reach the other groups in the class? You should be able to ping all the IPv4 and IPv6 loopbacks across the whole classroom.
Can you see the Internet too? The lab has IPv4 connectivity to the Internet - check that this works by trying a few pings or traceroutes to well known destinations (e.g. to 8.8.8.8).
The instructors will let you know if the lab has IPv6 connectivity. If it does, check IPv6 connectivity to the Internet as well, by trying a few pings or traceroutes to well know destinations (e.g. to 2001:4860:4860::8888).
Hint: for the traceroutes, try using the loopback address as the source for your pings and traceroutes.
Appendix - Transit Router Configuration
This appendix shows the minimum configuration used for the TR1 router in this lab. The TR2 router has a very similar configuration.
interface FastEthernet0/0
description Link to AS10
ip address 100.121.1.1 255.255.255.252
ipv6 address 2001:18:0:10::/127
!
interface FastEthernet0/1
description Link to AS20
ip address 100.121.1.5 255.255.255.252
ipv6 address 2001:18:0:11::/127
!
interface FastEthernet1/0
description Link to AS30
ip address 100.121.1.9 255.255.255.252
ipv6 address 2001:18:0:12::/127
!
interface GigabitEthernet4/0
description Link to TR2 (and to the world)
ip address 100.121.0.1 255.255.255.252 secondary
ip address 10.10.0.235 255.255.255.0
ipv6 address 2001:18::/127
ipv6 address 2001:DB8:100::235/64
!
router bgp 121
bgp log-neighbor-changes
bgp deterministic-med
no bgp default ipv4-unicast
neighbor 2001:18::1 remote-as 122
neighbor 2001:18::1 description eBGP with TR2
neighbor 2001:18::1 ttl-security hops 1
neighbor 2001:18::1 password BGPlab
neighbor 2001:18:0:10::1 remote-as 10
neighbor 2001:18:0:10::1 password BGPlab
neighbor 2001:18:0:11::1 remote-as 20
neighbor 2001:18:0:11::1 password BGPlab
neighbor 2001:18:0:12::1 remote-as 30
neighbor 2001:18:0:12::1 password BGPlab
neighbor 100.121.0.2 remote-as 122
neighbor 100.121.0.2 description eBGP with TR2
neighbor 100.121.0.2 ttl-security hops 1
neighbor 100.121.0.2 password BGPlab
neighbor 100.121.1.2 remote-as 10
neighbor 100.121.1.2 password BGPlab
neighbor 100.121.1.6 remote-as 20
neighbor 100.121.1.6 password BGPlab
neighbor 100.121.1.10 remote-as 30
neighbor 100.121.1.10 password BGPlab
!
address-family ipv4
network 100.121.0.0 mask 255.255.0.0
neighbor 100.121.0.2 activate
neighbor 100.121.1.2 activate
neighbor 100.121.1.2 default-originate
neighbor 100.121.1.6 activate
neighbor 100.121.1.6 default-originate
neighbor 100.121.1.10 activate
neighbor 100.121.1.10 default-originate
distance bgp 200 200 200
exit-address-family
!
address-family ipv6
network 2001:18::/32
neighbor 2001:18::1 activate
neighbor 2001:18:0:10::1 activate
neighbor 2001:18:0:10::1 default-originate
neighbor 2001:18:0:11::1 activate
neighbor 2001:18:0:11::1 default-originate
neighbor 2001:18:0:12::1 activate
neighbor 2001:18:0:12::1 default-originate
distance bgp 200 200 200
exit-address-family
!
ip route 0.0.0.0 0.0.0.0 10.10.0.254
ip route 100.121.0.0 255.255.0.0 Null0
!
ipv6 route 2001:18::/32 Null0
ipv6 route ::/0 2001:DB8:100::241
!